TrustSEC and HID® Partner to Deliver the Next Generation of Biometric Smart Cards
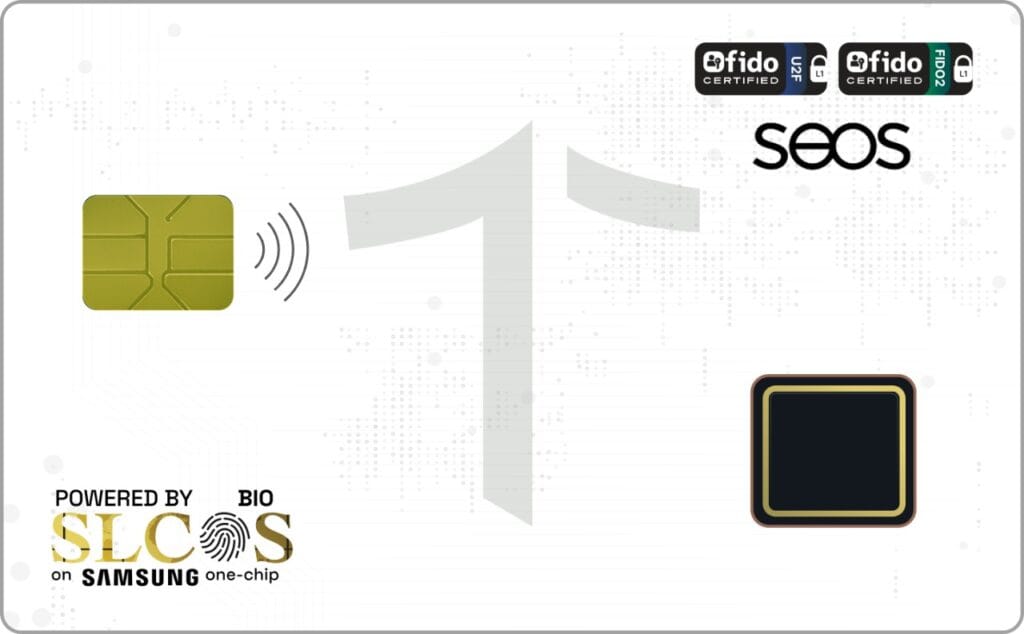
Converged identity is entering a new era. TrustSEC is proud to announce a strategic partnership with HID® to develop the SAMSUNG One-Chip Bio Smart Card, powered by the TrustSEC Java Card BIO SLCOS and featuring the HID® Seos® applet. This groundbreaking solution represents the ultimate evolution in secure, converged identity, engineered for maximum assurance, privacy, and user convenience. A New Standard in Converged Identity As organizations demand stronger security without sacrificing usability, traditional access cards are no longer enough. The SAMSUNG One-Chip Bio Smart Card delivers a single, secure credential that seamlessly combines: Physical access control Logical (IT) access On-card biometric authentication By unifying these capabilities into one credential, TrustSEC and HID® are redefining how enterprises and governments approach identity assurance. Powered by TrustSEC Java Card OS and HID® Seos® At the core of this advanced smart card is the TrustSEC Java Card, BIO SLCOS, designed to meet the highest standards for secure identity applications. The inclusion of the HID® Seos® applet ensures compatibility with industry-leading access control systems while maintaining flexibility for future identity use cases. This powerful combination enables organizations to deploy a future-proof, standards-compliant identity solution that integrates effortlessly into existing infrastructures. True On-Card Biometric Security What truly sets the SAMSUNG One-Chip Bio Smart Card apart is its innovative all-in-one chip architecture. The card integrates: A fingerprint sensor A Secure Element (SE) A Secure Processor This unique design allows biometric matching to occur entirely on the card. The user’s fingerprint data never leaves the secure environment, eliminating the risks associated with external biometric processing or data transmission. Key Security Benefits: Biometric data is stored and matched securely on-card No biometric data is shared with readers or backend systems Reduced attack surface and enhanced privacy protection Compliance with strict enterprise and government security requirements Designed for High-Assurance Environments The SAMSUNG One-Chip Bio Smart Card is engineered for the most demanding enterprise and government applications, including critical infrastructure, regulated industries, and high-security facilities. By combining biometrics, cryptographic security, and trusted access technologies in a single credential, organizations can achieve: Strong multi-factor authentication Seamless user experience Improved identity lifecycle management Higher levels of trust and compliance The Future of Secure Identity The partnership between TrustSEC and HID® marks a significant milestone in the evolution of secure identity solutions. The SAMSUNG One-Chip Bio Smart Card delivers a seamless, highly secure, and user-centric authentication experience, setting a new benchmark for converged physical and logical access control. As identity threats continue to evolve, solutions like this ensure organizations stay ahead—without compromising security, privacy, or usability.
Wrap up of TrustSEC at TRUSTECH 2025

The energy and innovation at TRUSTECH 2025 in Paris were truly unmatched! TrustSEC was honored to exhibit at Booth E042 from December 2nd to 4th, and we extend our sincere gratitude to everyone, from partners and clients to new contacts, who contributed to our most successful presence yet. Spotlight: Sustainable Smart Card At our booth, we shared an overview of our next-generation biometric smart card and how it reflects our broader vision for secure and responsible authentication. Conversations centered on the growing need for solutions that balance strong security with ease of use, privacy, and sustainability. Our next-generation biometric smart card represents this balance by bringing advanced biometric authentication directly onto the card, reinforcing a privacy-first approach while reducing environmental impact through more sustainable design choices. Designed as a flexible platform, our next-generation biometric smart card is positioned to support a wide range of access, identity, and payment use cases, making it a strong fit for today’s evolving digital ecosystems. Strategic Partnership Showcase: TrustSEC and HID Global A cornerstone of our presence was the collaboration with global security leader HID Global. We were extremely proud to feature a live demonstration illustrating the seamless integration of TrustSEC’s secure operating system (BIO-SLCOS) and smart card technology with HID Global’s ecosystem. This demo highlighted how our combined expertise enables: Instant, Secure Access: Showing how a secure biometric smart card can be deployed instantly for high-security access control, leveraging established HID reader infrastructure. Next-Gen Identity Solutions: Demonstrating a real-world application that fuses strong, privacy-preserving biometric authentication with global standard infrastructure, setting a new benchmark for secure identity management. The Collaboration Ecosystem In addition to our key showcase with HID Global, we were delighted to host and collaborate with other esteemed partners at our booth: Ligna Energy: Showcasing sustainable power solutions through their bio-based, lithium-free supercapacitors. Wibiocard: Demonstrating cutting-edge expertise in biometric access and authentication. eSignus: Presenting innovations in cryptographic security, including advanced hardware wallets like the HashWallet. Dongwoon Anatech: Discussing their role in the scalable production of secure, biometric smartcards. The Road Ahead: Building on Trustech Momentum The discussions held and the partnerships formed over these three days are already generating momentum. We are more confident than ever that TrustSEC, alongside partners like HID Global, is uniquely positioned to lead the secure authentication market, delivering solutions that comply with global standards like GDPR, eIDAS, and critical ESG mandates. Thank you for being part of this exciting chapter. We look forward to realizing the full potential of these collaborations in the coming year and seeing you all again at TRUSTECH 2026!
TrustSEC x Samsung One-Chip: One Year Later — Turning Innovation Into Market-Ready Reality 🔐💳

A year ago, we introduced our breakthrough smart card OS built for the Samsung One-Chip platform. Today, that vision has evolved into a fully optimized, production-ready biometric smart card foundation trusted by partners and integrators worldwide. Over the past 12 months, our joint work with Samsung Electronics has accelerated on every front performance, security, interoperability, and customization. The result: a platform that doesn’t just push the boundaries of technology, but makes biometric card deployment simpler, faster, and more scalable than ever. What’s New This Year * Optimized OS architecture delivering faster biometric matching and reduced power consumption * Expanded SDK toolset enabling integrators to tailor use cases in payments, access control, identity, and IoT security * Advanced secure processing pipeline with improved anti-spoofing and runtime protections * Certification-ready design aligned with industry security schemes and EUDI requirements * Multiple partner evaluations and pilots proving the platform’s readiness for real-world adoption Why it Matters 1-Organizations are looking for strong authentication, that is: 2-Ultra-secure 3-User-friendly 4-Easy to integrate 5-Future-proof for digital identity ecosystems TrustSEC’s customizable OS on Samsung One-Chip delivers exactly that—a unified biometric smart card platform engineered for both high performance and high assurance. Driving the Next Chapter of Biometric Innovation As demand for secure, flexible authentication grows across payments, access control, mobility, and government identity, we remain committed to enabling partners with technology that adapts to their needs—not the other way around. If your roadmap includes next-generation biometric cards or identity solutions, we’re ready to help you build what’s next. #TrustSEC #SamsungOneChip #BiometricSmartCards #SmartCardOS #SecureIdentity #AccessControl #PaymentSecurity #BiometricInnovation #DigitalIdentity #FingerprintTechnology #NextGenerationSecurity
Building Zero-Trust Environments with Biometric PKI Tokens & SLCOS

Zero-Trust Security is no longer a buzzword, it is a business imperative. As perimeter-based defenses crumble, modern organizations increasingly rely on hardware-rooted identity systems that verify every interaction, device, and session. TrustSEC’s unique combination of biometric PKI tokens and flexible SLCOS smart card operating system delivers this robust, zero-trust foundation. 1. What is Zero-Trust — and Why Software-Only Fails Zero-Trust rejects outdated “trust but verify” models. Instead, every access request must be authenticated, authorized, and encrypted regardless of origin. Relying on software-based credentials like passwords or OTP is becoming too risky: Phishing and malware can hijack credentials from devices. SIM-swap attacks enable attackers to intercept SMS-based OTPs; these surged 400% from 2020 to 2023. Complaints grow as enterprises recognize that software tokens introduce too many vulnerabilities. To thrive in a zero-trust world, hardware-backed identity is essential. 2. The Power of Biometric PKI Tokens TrustSEC’s biometric PKI tokens provide hardware-level protection and user-specific verification. Here’s why they are transformative: Biometric match-on-card (MoC) ensures that fingerprints are verified directly on the secure element; no data ever leaves the device. Secure storage of cryptographic keys prevents extraction via malware or remote attack. With FIDO2 smartcard compatibility, these tokens support passwordless login and strong authentication. This ensures every access request meets zero-trust standards. 3. How SLCOS Empowers Custom Solutions The SLCOS (Smartcard Operating System) platform serves as the engine powering TrustSEC’s security ecosystem: Supports Java Card / GlobalPlatform standards. Offers adaptability, IoT-optimized, biometric-enabled, PCI-compliant card OS. Simplifies feature implementation: FIDO2, PKI, PKC algorithms, C-PACE/D-CrEPT/Z-something for e-sign. This flexibility enables partners to build custom authentication solutions tailored for fields like finance, IoT, and public sector. 4. Real-World Use Cases Enterprise Access Security Organizations deploy biometric PKI tokens across employee devices. These tokens enable secure VPN and desktop login, enforce MFA without passwords, and comply with strong authentication mandates. IoT Device Authentication In IIoT environments, lightweight SLCOS applets verify device identity during firmware updates or data transmission. SLCOS’s small footprint and off-line capability make it ideal for edge deployments. Critical Infrastructure Airports, utilities, and government sites deploy biometric access control cards powered by SLCOS to secure gates, labs, and control rooms — even those that are air-gapped. 5. TrustSEC’s Complete Zero-Trust Offering TrustSEC’s bundled solutions simplify zero-trust adoption: Identity Wallet Suite — Secure issuance, PKI key management, FIDO2 smartcard, and biometric identity. Enterprise Access & Data Protection Bundle — Biometric USB tokens, RADIUS integration with Azure AD, and centralized authentication tools. eGov Digital Trust Kit — Includes SLCOS cards, e-signature solutions, and PKI-backed audits. These comprehensive bundles cover all facets of zero-trust infrastructure. 6. Why It Works — Trusted, Compliant, Future-Ready TrustSEC’s strength lies in: Hardware-rooted biometric security. Full PKI integration for cryptographic validation. European data privacy and regulatory compliance (GDPR, eIDAS). Flexible SLCOS OS for customized deployment or OEM integration. This makes TrustSEC’s approach ideal for organizations building resilient, zero-trust systems. 7. Deploying Zero-Trust with TrustSEC Step 1: Needs Assessment — Define user groups, device types, and regulatory needs. Step 2: Bundle Selection — Choose from Identity Wallet, Access Bundle, or eGov Kit. Step 3: Issuance & Enrollment — Distribute tokens or cards and register biometrics securely. Step 4: Infrastructure Integration — Connect with SSO, VPN, Azure AD, or PKI systems. Step 5: Monitor & Expand — Use analytics and audit tools to validate performance and plan future rollouts. 8. Summary Zero-trust environments do not just happen — they are engineered, credential by credential. TrustSEC’s biometric PKI tokens and versatile SLCOS smart card OS offer a secure, compliant, and scalable foundation. Whether it is enterprise, IoT, or government use, this solution delivers proven zero-trust identity across sectors. Ready to build a zero-trust future? Explore our bundles, request a demo, or contact us today.
FIDO2 Smartcard Applet

FIDO2 Smartcard Applet Smart cards have become a fast-growing market due to the higher demand for tighter security measures. It also became mandatory in governmental and fintech services’ digital transformation. Smartcards now contain end-users personal data (e.g. health, social security, digital identity, crypto transactions, etc) FIDO2 Applet on Java Card Java Card: A Multi-Application Operating System for Smart Cards It allows applets) to be loaded and securely executed on-chip card systems. Java Card is a very small subset of Java platforms that can be used on embedded devices such as smart cards with small memory and CPU footprint devices. Java Card has been around for over 20 years now. It is a mature smart card operating system. Applet load, initialization, personalization, and deletion heavily rely on Global Platform specifications. Java Card is an open, multi-application operating system for smart cards. Diverse parties can develop applications for the same smart card using their respective Java programming skills. The resulting applets run on the same card and co-reside independently. Thus, applications from various vendors can be combined after being separately developed. Fast Identity Online FIDO2 is the umbrella term for a passwordless authentication open standard developed by the Fast Identity Online (FIDO) Alliance, an industry consortium comprised of technology firms and other service providers. FIDO 2 consists of two core components. The first is the WebAuthn API, which industry leaders are incorporating into their browsers, including Chrome, Edge, Mozilla, and WebKit. Second, there’s the Client to Authenticator (CTAP) protocol that provides FIDO 2-capable devices an interface for external authenticators via NFC, USB, or Bluetooth. Solutions built atop FIDO2 undergo rigorous certification to ensure that user credentials are decentralized, isolated and encrypted on users’ personal devices. TrustSEC FIDO2 Applet Based on the above, TrustSEC offers its FIDO2 java card Applet to all business owners who have a smartcard solution integrated with web-based services and would like to secure their end-users logins over the web. It corresponds to the requirements for secure authentication that are integrated/activated with smartcards and could exist on the card in addition to other applets to help businesses provide a secure turnkey solution. It could easily be intended for production over any java smart card operating system. FIDO2 Smartcards could be a 2-factor-authentication or Multi-factor authenticator based on the biometric feature addition Something you are ( Fingerprint ), however, the 2Fa FIDO2 Smartcards will be a combination of something you have (the smart card) with something you know (a secret, the smart card PIN). FIDO2 Authentication Process The user registers to a web application or services, His/Her registration generates a public key and a private key. When requesting access to the web service, a challenge is generated, then the challenge is signed and returned using the keys pairing part over the smartcard which is created in the smart card and never leave it. When the right key pair is used, the user can successfully log in. Also, a great advantage of using one FIDO2 Authenticator Applet is the possibility of multiple logins to different applications, while only one PIN/fingerprint is required to enable access to the authenticator. FIDO2 Smartcard Applet Security keys Check TrustSEC Security keys range to choose from single-factor, two-factor, or multi-factor keys for secure login, over different platforms for different verticals with a variety of authentication scenarios. Fido2 Security Keys Biometric Fido2 Smartcard TrustSEC Fido2 Smartcard What is FIDO2 Smartcard Applet? Smart cards have become a fast-growing market due to the higher demand for tighter security measures. It also became mandatory in governmental and fintech services’ digital transformation. Smartcards now contain end-users personal data (e.g. health, social security, digital identity, crypto transactions, etc) FIDO2 Applet on Java Card Java Card: A Multi-Application Operating System for Smart Cards It allows applets) to be loaded and securely executed on-chip card systems. Java Card is a very small subset of Java platforms that can be used on embedded devices such as smart cards with small memory and CPU footprint devices. Java Card has been around for over 20 years now. It is a mature smart card operating system. Applet load, initialization, personalization, and deletion heavily rely on Global Platform specifications. Java Card is an open, multi-application operating system for smart cards. Diverse parties can develop applications for the same smart card using their respective Java programming skills. The resulting applets run on the same card and co-reside independently. Thus, applications from various vendors can be combined after being separately developed. Fast Identity Online FIDO2 is the umbrella term for a password less authentication open standard developed by the Fast Identity Online (FIDO) Alliance, an industry consortium comprised of technology firms and other service providers. FIDO 2 consists of two core components. The first is the WebAuthn API, which industry leaders are incorporating into their browsers, including Chrome, Edge, Mozilla, and WebKit. Second, there’s the Client to Authenticator (CTAP) protocol that provides FIDO 2-capable devices an interface for external authenticators via NFC, USB, or Bluetooth. Solutions built atop FIDO2 undergo rigorous certification to ensure that user credentials are decentralized, isolated and encrypted on users’ personal devices. TrustSEC FIDO2 Applet Based on the above, TrustSEC offers its FIDO2 java card Applet to all business owners who have a smartcard solution integrated with web-based services and would like to secure their end-users logins over the web. It corresponds to the requirements for secure authentication that are integrated/activated with smartcards and could exist on the card in addition to other applets to help businesses provide a secure turnkey solution. It could easily be intended for production over any java smart card operating system. FIDO2 Smartcards could be a 2-factor-authentication or Multi-factor authenticator based on the biometric feature addition Something you are ( Fingerprint ), however, the 2Fa FIDO2 Smartcards will be a combination of something you have (the smart card) with something you know (a secret, the smart card PIN). FIDO2 Authentication Process The user registers to a web application or services, His/Her registration generates a public key and a private key. When requesting access to the web service, a
Biometric Access control cards

TrustSEC Biometric Access control cards release We are happy to announce the release of TrustSEC Bio Access control card. The Access control card will facilitate the users’ authentication experience with guaranteeing high-security measures. Organizations across every industry seek dependable, practical, and secure solutions for identification. If you think Physical and logical options are broad, the choice can be overwhelming. TrustSEC’s Bio access control cards combine both functionalities. This solution simplifies the authentication process, by successfully authenticating the person’s identity over physical access points and logical access with the user’s unique fingerprint. Access control physical vs. logical access Access control is the selective restriction of access to a location or other resource. It is used to regulate individuals’ views, access, or use of specific resources and/or information. The two main types are physical and logical. Physical access control is the selective restriction of access to a site, which is often performed through a range of security mechanisms that regulate and track who enters and leaves a facility. smartcards are one of the top technologies used in Physical access control systems. Logical access control is managing/restricting virtual access to data; it includes identification, authentication, and authorization protocols to identify who has the right to access a specific software or hardware. Logical access control mechanisms are dependent on many factors, such as passwords (Something you know), smart cards, tokens (something you have), and biometrics (something you are). The three factors when used together provide the highest security levels. Biometric Authentication on the card The biometric technology used on the cards depends on the Match-on-Card (MoC) feature that will store the holder’s biometric data and protect such communications with encryption. TrustSEC Biometric smartcards demonstrate a high level of flexibility as the technology used within the card is adaptable enough to integrate with any applet, is durable enough to last for many years, and provides user-friendliness; the card’s portability makes it easy for users to carry in their wallet. In addition to the automated Identification, and Access Control Solution, other applets could also be Personalized on the card for example applet for Secure Document Exchange. The solution would be vital for governments, banks, and enterprises where high-security measures are a must. TrustSEC Bio Access control cards’ reliability and durability will replace the complexity of the day-to-day operations with just one card. For more information, please contact us at info@trustsec.net
