TrustSEC FIDO2 Applet
Achieve passwordless, phishing-resistant authentication via FIDO2 on Java Card.
Key Features
- Enables passwordless and multi-factor authentication with biometric or PIN verification
- FIDO2 CTAP2.1 compliant, working across browsers and OS (via WebAuthn + CTAP)
- Smartcard-based—no biometric or credential data leaves the secure element
- Can co-reside with other Java Card applets on the same card
- Compact, OEM-ready applet for enterprise or public sector deployments
- GDPR and eIDAS compliant with strong European privacy safeguards
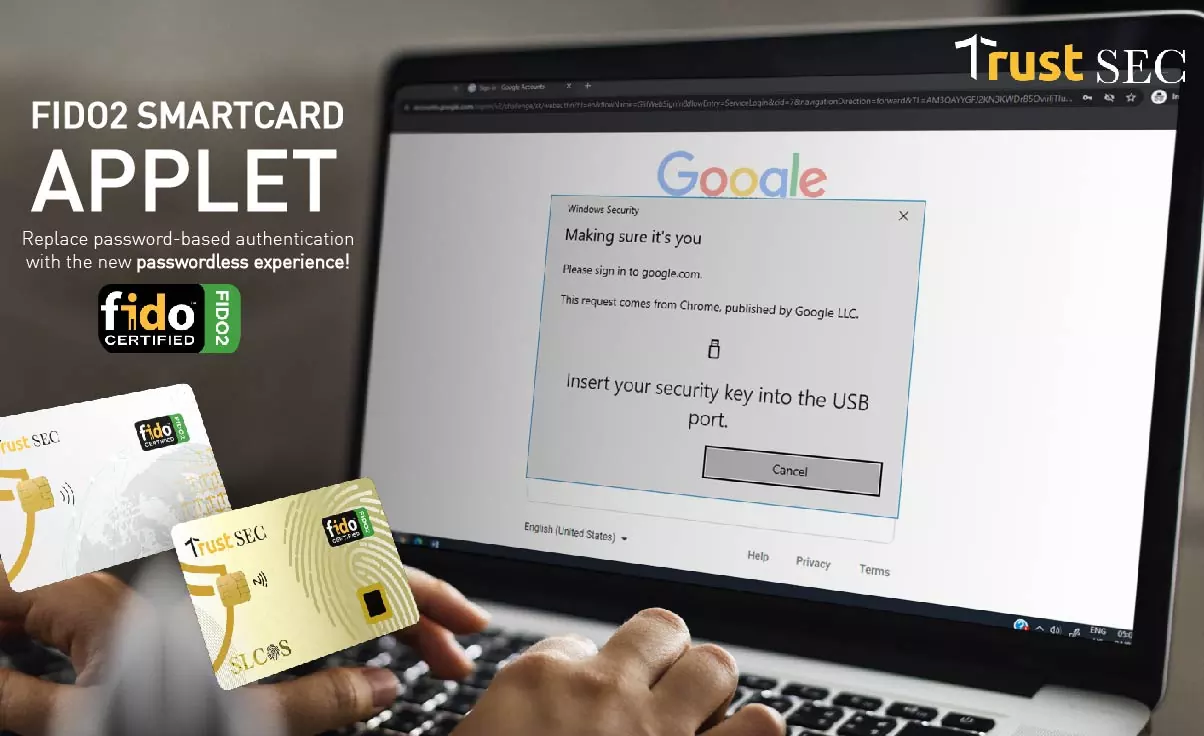
FIDO2 Authentication
What is FIDO2 Authentication?
FIDO2 is an open standard from the FIDO Alliance that enables passwordless login via public-
key cryptography. It relies on WebAuthn (browser-side API) and CTAP (smartcard/device
protocol) for secure authentication. With TrustSEC’s Java Card applet, keys never leave the card
—ensuring decentralized and phishing-resistant credentials trustsec.net.

Why TrustSEC FIDO2 Applet?
Why TrustSEC FIDO2 Applet?
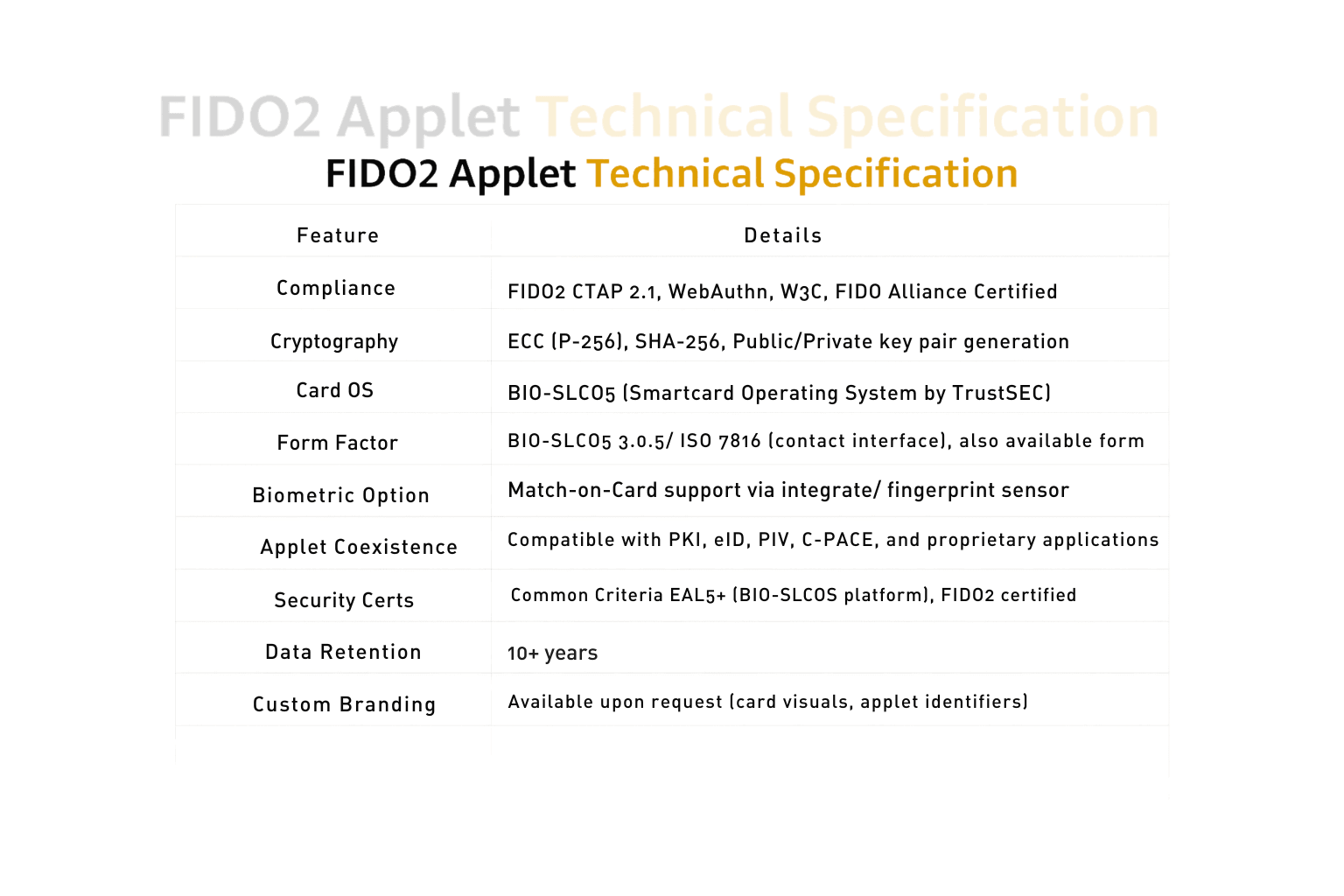
- BIO–SLCOS Integration: Optimized for our secure smartcard OS (BIO–SLCOS),
supporting match-on-card workflows. - On-card Biometrics: Supports fingerprint or PIN verification entirely on device—secure
and privacy-preserving. - Multi-Applet Coexistence: Smartcard OS supports multiple independent applets via
GlobalPlatform standards trustsec.net. - Enterprise Trust: Ideal for financial, government, or critical infrastructure use, with
certified FIDO2 and strong European compliance.

Use Case
Use Case
Cases
Use Cases:
- Secure enterprise logins (VPN, domains, desktops).
- Government/public sector authentication (eID, e-signature).
- Financial login (PSD2, MFA).
- Multi-application smartcards (credentials + e-ID + payment)

FAQ
FAQ
A modern, passwordless login standard based on public-key cryptography, using
WebAuthn and CTAP.
Fingerprint templates are stored and matched directly on the card; no sensitive
data leaves the card surface
Yes. BIO-SLCOS + GlobalPlatform allow multiple independent applets (eID,
PKI, payment, etc.
It’s a proven, secure platform that ensures compatibility and multi-applet
flexibility arXiv+2trustsec.net+2arXiv+2.
USB, NFC, BLE—compatible across devices and major platforms.
